Enterprise Incident Management | In-Depth Guide
Enterprise incident management is, without doubt, one of the most important responsibilities of IT teams in large organizations.
This is because IT incidents can potentially have an enormous impact on the wider business. In fact, in extreme situations, it could easily be lights out. Even if it’s not this dramatic, we still risk data loss, service interruptions, and, ultimately, lost revenue.
Today, we’re going deep into managing IT incidents in an enterprise context.
Specifically, we’ll kick off by thinking about what incident management actually means and what it achieves. We’ll also think about the key types of incidents that we’ll want to build our response processes around.
Then, we’ll move on to presenting a reproducible framework that we can build our enterprise incident management efforts around, before checking out the key tools that we’ll need to facilitate this.
Lastly, we’ll wrap up by seeing how Budibase empowers enterprise IT teams to provide exceptional internal services at pace.
Let’s start with the basics.
What is enterprise incident management?
Enterprise incident management comprises all of our efforts to predict, prevent, respond to, document, and learn from IT incidents.
We’ll cover what these incidents might be in more detail a little later, but for now, we can simply think of an incident as something going wrong. This could be a fire, a website outage, a security attack, or a huge range of other issues.
The core challenge here is that we can’t expect IT incidents to follow a specific pattern. By their nature, incidents are difficult to predict, both in terms of when they occur and what we need to do to correct the situation.
As such, it’s helpful to break incident management into two strands:
- Proactive - Routine tasks aimed at identifying, mitigating, and eliminating risks of common incidents, including auditing, monitoring, testing, training, and risk assessment workflows.
- Reactive - Responses to specific incidents, including assessing the situation, formulating and executing a response, documenting learnings, and sharing information about how similar incidents can be prevented in the future.
Ultimately, the goal of incident management is to minimize the wider business impact of issues with our IT ecosystem.
Let’s think about how this works in a little bit more detail.
Benefits
Enterprise incident management achieves several business-level benefits.
The key here is understanding the impact that IT incidents can have. Some of the most common risks and threats here include security breaches, service interruptions, data loss, physical damage, personal injury, or other errors and mistakes.
Any of these can lead to a variety of financial, reputational, operational, and legal issues, such as lost revenue, negative PR, lawsuits, disruption, and more.
The primary benefit of incident management for enterprises is responding to problems in order to minimize these issues.
On top of this, another key benefit is systematizing learnings from incidents and potential incidents. In turn, this facilitates process changes, additional mitigations, or other measures that can help prevent similar incidents from reoccurring.
As with any ITSM process, our incident management efforts also have an impact on our wider operational efficiency. That is, when we’re able to reach effective resolutions quickly, our IT team and business colleagues alike are able to focus on more productive tasks.
You might also like our round-up of the top free asset management software.
Challenges
However, there are several issues that can easily impede our incident responses, especially in an enterprise context.
Here are some of the key blockers we’ll need to overcome.
Data centralization
The first challenge for enterprise incident management is establishing clear oversight of the relevant data. The difficulty here is that we’re potentially dealing with huge, highly distributed data sets.
For instance, even getting a grip on all of our devices by creating a database for hardware asset management is a huge challenge. On top of this, we’ll also need to centralize data concerning users, software, data assets, infrastructure, processes, and more.
As such, the first step to effectively handling incidents is getting our wider ITSM operations in order, particularly with regard to building an enterprise data model. Take a look at our guide to ServiceNow alternatives to learn more about the solutions landscape here.
Identifying incidents
Another huge pain point is identifying when an incident has occurred. In a small minority of cases, this can be self-evident. For example, if there’s a fire or a flood in our server room.
More often, though, we’ll need to take a more active approach to identifying incidents. How this works varies between different kinds of incidents. For many software, networking, security, and product issues, we’ll typically leverage some combination of monitoring and automated alerts.
For other kinds of incidents, including breakages, data breaches, phishing scams, and other end-user issues, we’ll need some mechanism for receiving reports from affected colleagues. For example, using incident reporting forms.
That leads us to…
Service-user buy-in
Arguably, one of the biggest stumbling blocks for enterprise incident management is actually getting users to tell us when something goes wrong. Often, this means we can’t implement a response until the incident has already started to cause issues.
There are a couple of key reasons why users might fail to report incidents. One is a fear of repercussions. That is, they might be concerned that they will be blamed for the incident occurring, so they don’t report it.
The more common issue, however, is a simple failure to understand the need to report incidents or how they can go about this. Strategies for overcoming this include end-user awareness training as well as effective self-service IT portals.
Documenting outcomes
Lastly, the aspect of incident management that many teams struggle the most with is documenting outcomes and solidifying learnings. The goal is that, with each incident we respond to, we should be building a repository of knowledge to facilitate future improvements.
In the real world, though, it’s more common for learnings to be limited to the service agents involved in responding to a particular incident. This can make it difficult to garner insights or identify opportunities to improve our processes.
There are a range of strategies we can leverage to overcome this. In the first instance, our priority must be thoroughly documenting our experience around an incident, including its cause, contributing factors, impact, and eventual resolution.
We must then have tools in place to share this information with relevant stakeholders, both at the level of individual incidents and by aggregating data to identify trends in how and when issues occur.
For example, we might use a knowledge base to record information relevant to preventing different incidents.
8 types of IT incidents
Earlier, we said that an IT incident is any issue that occurs with the potential to harm our organization financially, legally, reputationally, or operationally.
However, we can break this down into more detailed categories of incidents based on the kinds of assets involved, the extent of the issues, and the impact they’re likely to have.
The most common types of IT incidents include:
- Hardware incidents - Incidents affecting physical devices, including end-user devices, peripherals, network infrastructure, data storage, or other hardware.
- Software incidents - Incidents relating to our software tools, including breakages, bugs, outages, or other issues.
- Data loss - Including malicious or accidental deletion.
- Unauthorized access - Users gaining access to our tools, data, or processes outside of defined authorization and authentication policies.
- Denial of service - Malicious attempts to make our IT system unusable.
- Service interruptions - Other interruptions to our services, whether malicious or accidental, including network outages, vendor-side issues, or power outages.
- Malfunctions - Issues relating to devices and assets malfunctioning, either at a software or hardware level.
- Physical incidents - Physical issues that might result in damage to devices or injury to colleagues, including floods, fires, and falls.
We’ll also need to consider different kinds of incidents in terms of their severity and the extent of the potential impact.
Some teams will have complex rules and frameworks for assessing and ranking the severity of incidents. More commonly, though, these are ranked on a high/medium/low scale.
We’ll then typically see distinct response flows for different levels of severity. We’ll cover this in more detail shortly.
Enterprise incident management process in 7 steps
Now that we have a strong grasp of enterprise incident management in terms of the kinds of issues we’re most likely to contend with, as well as the business-level benefits we can expect through improving our efforts here.
Next, we can think about the specific framework that we can rely on to respond to specific incidents.
1. Identifying and logging incidents
The first step is identifying that an incident has occurred. As we said earlier, there are two key strategies available to us here.
First of all, we can proactively monitor for incidents occurring. However, this is limited to certain kinds of incidents, such as network outages, some security breaches, power issues, and other infrastructure issues.
For many of these, monitoring can be fully automated, including setting up alerts when an outage occurs.
Other proactive monitoring might require more human input. For example, analytics data outside of our normal values for metrics surrounding usage, data access, or other day-to-day operating data might be indicative of a potential issue our team needs to investigate.
Then, we have reactive strategies.
Essentially, this means providing channels for end users to report incidents. We can go about this in a couple of different ways, but in reality, we’ll likely need to take a combined approach.
The first is providing forms explicitly for reporting incidents. These can be standalone tools, or they might be provided as part of a wider IT portal or service-specific app, such as an asset management tool.
The goal is to furnish users with a fast, easy way to submit information about incidents in a defined format that’s usable for the IT team.
We’ll also leverage other kinds of user interactions in order to identify incidents. For example, within our normal service desk or ticketing system flows, we might provide capabilities to flag an issue as a potential incident.
2. Categorizing issues
Once an incident has been identified, our first task is to categorize it so that we know the appropriate team to route it to. In some cases, this could be somewhat self-evident, but in others, it will require more investigation.
For instance, with something like a network interruption or a power issue in a data center, our response will almost certainly come from our infrastructure team.
More often, though, we’ll need to make an active decision about which team to route a potential incident to.
However, the specifics of this will vary from one organization to the next.
That is, as part of our enterprise incident management strategy, we’ll need to define a taxonomy for incidents. This includes the categories we’ll place them into, along with the criteria for each one.
What’s tricky here is the fact that this must be informed both by the types of incidents we expect our IT estate to be vulnerable to, as well as resourcing and operational concerns across our IT team.
A simple framework might involve categorization at the point of submission, for instance, asking service users to identify whether their ticket relates to hardware, software, data, etc. Service desk colleagues can then more granularly route this to specific teams.
3. Incident prioritization
Next, we have incident prioritization. Essentially, this means determining how serious an incident is in terms of its potential impact on service users, customers, or the business as a whole.
We’ll need to consider this both in absolute terms and relative to our other incidents and wider IT workload.
Just like with categorization, the actual prioritization matrix will be specific to our internal workflows. As we said earlier, we might use a simple high/medium/low framework for prioritizing incidents.
For example, a high-priority incident might be mission-critical, whereas lower-priority issues only relate to individual users or tasks.
Alternatively, we might opt for a more detailed, granular framework. For instance, a numerical scale.
In any case, our incident prioritization is critical for determining how to proceed with formulating a response.
Specifically, we’ll use this to allocate resources, prioritize tasks, and decide which specific workflows and mitigations we need to initiate, including comms, backups, and other incident-specific tasks.
4. Investigation and diagnosis
The next stage of our enterprise incident management is investigating and diagnosing the cause so that we can formulate a response.
For certain kinds of incidents, we might have a defined playbook. This is particularly common with networking and infrastructure issues. Service agents might simply be able to follow a defined sequence of actions to find the fault at hand.
However, we can’t always rely on this. By their nature, incidents are unpredictable, and many of them will fall outside of defined patterns.
As such, the reality is that we can define processes for investigating incidents, but the substance of the diagnosis itself will inevitably be highly specific to individual incidents.
Broadly though, this could involve analyzing usage data, audit logs, code bases, access history, and other relevant information. The key, therefore, is recording data that could be relevant to incident investigations in a centralized, accessible location.
5. Restoring service
Once we’ve investigated an incident and diagnosed the fault that caused it, our priority is restoring service.
There are potentially a few aspects to this, depending on the nature, severity, and complexity of the incident.
In some scenarios, we might need to implement temporary fixes in order to restore services in the immediate term, with a more long-term solution coming later. For example, putting a mitigation in place until we’re able to roll out a security patch.
In other cases, our resolution could be more straightforward. For instance, if the root cause was a bug or network issue that only requires a simple fix.
In the case of hardware and device-related incidents, this can look a little bit different. Say, for example, that we were dealing with physical damage to an end-user device. In this case, restoring service could be a simple matter of replacing the affected hardware.
In any case, another key aspect of enterprise incident management here is communicating timelines, expectations, and impact to stakeholders. This is critical at all stages of our response, from when an incident is identified until service is restored.
6. Conducting a post-mortem
Once service is restored, our focus shifts from the incident itself to the conditions that enabled it to occur.
The goal here is to identify opportunities for improving our processes or tech stack to prevent similar incidents from occurring in the future.
It’s important to distinguish the cause of the incident from the environment in which it happened.
For example, a data loss incident might occur because of human error. However, this might only have been a possibility because of issues with our wider data operations, such as over-reliance on spreadsheets for mission-critical tasks.
Or, the root cause of an incident could be poor compliance with an internal process, which could have been avoided with better end-user training.
7. Documenting and implementing learnings
The last step in our enterprise incident management process is documenting and implementing what we’ve learned.
For documentation, the key is providing service agents with tools to record relevant information in a structured format. For instance, by utilizing dedicated data collection forms for submitting reports.
We can then use this information to inform future decision-making, based on individual incidents and at an aggregated level.
Implementing learnings largely means implementing process changes, new technologies, training programs, or other measures aimed at reducing the risk of future incidents.
Similarly, we should also seek out lessons relating to how we can reduce the impact of a certain type of incident where it can’t be prevented entirely. For example, reducing our reliance on a particular platform or piece of hardware to reduce the impact of outages.
6 tools for managing incidents
Now that we know exactly what we need to achieve at each stage of the enterprise incident management process, our next task is to think about the specific tools that we’ll need along the way.
As incident management cross-cuts with a huge range of other ITSM processes, it’s highly likely that we’ll rely on a combination of dedicated workflow tools and existing platforms to provide the capabilities we need.
In any case, here are the specific types of solutions that are most commonly leveraged within incident management workflows.
Incident report forms
Incident report forms are something we’ve alluded to several times already. In very simple terms, these are UIs that allow users to submit information about an incident in a structured format, creating a record in a database.
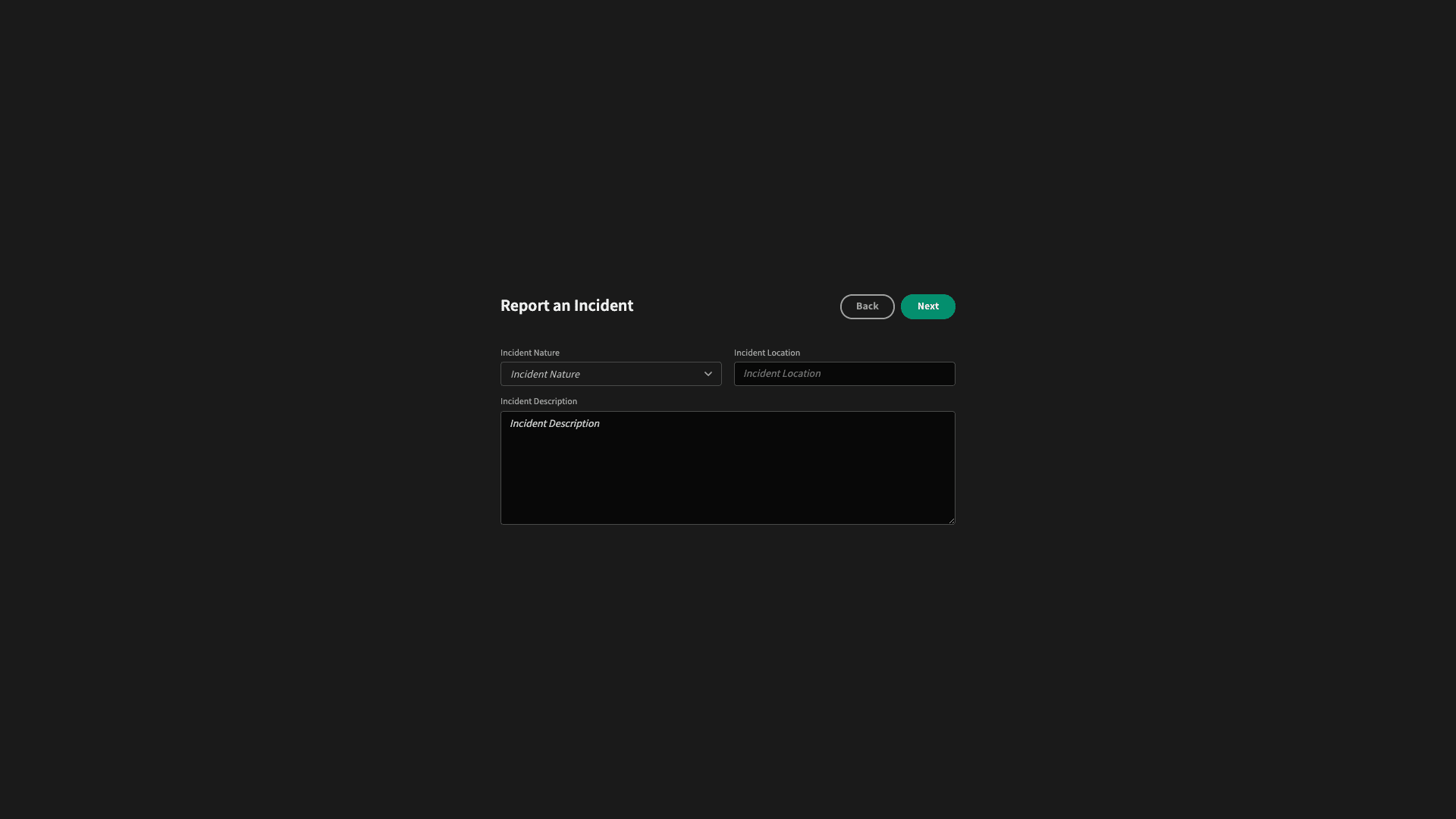
The goal is to provide an accessible, streamlined way for users to submit accurate, timely incident reports.
But there’s more to this than meets the eye. We might want to leverage relatively advanced form UIs in order to gather information relevant to different kinds of incidents using conditional logic.
We’ll also need to consider how and where our incident data is saved, along with any follow-on process that might need to be initiated upon form completion.
Check out our forms page to learn more about what Budibase brings to the table here.
Ticketing systems
Ticketing systems are at the core of just about every ITSM workflow. These are tools that allow service users to submit requests which can then be picked up, managed, and actioned by service desk colleagues within the IT team.
In the context of incident management, ticketing can play a couple of key roles.
The most obvious is if we provide explicitly incident-focused ticketing capabilities. This is essentially an incident report form with additional capabilities for responding to and managing reports within a single platform.
However, our day-to-day support and trouble ticketing also have a role to play. That is, issues reported by end-users can be indicative of an incident, without the colleague reporting this realizing.
Therefore, it’s crucial that we have incident-flagging capabilities integrated into our ticketing tools for service agents to escalate issues.
Monitoring tools
As we’ve said several times already, many kinds of incidents can be identified using monitoring tools.
These are automation solutions that trigger alerts when some defined condition is met.
These might even be built into existing tools. For instance, outage alerts for infrastructure hardware.
In other cases, we may need to define our own automations. For instance, triggering an alert if a database action is carried out outside of a defined pattern.
Dashboards
Dashboards are internal tools that provide real-time updates on specific metrics. This can include a range of read-outs and visualizations, depending on the topic of the specific report at hand.
The idea is to enable colleagues to quickly check the status of key metrics without needing to run the reports manually each time.
For enterprise incident management, we might rely on several different kinds of dashboards to help us identify when something has gone wrong.
A simple example would be providing uptime data for servers or data center infrastructure.
However, just about an ITSM dashboard can provide useful insights for helping us identify incidents, especially when they display data outside of normal or expected values.
Workload management
Workload management tools are used to allocate resources and schedule specific tasks. We can then assign specific issues and actions to different colleagues. This is a critical part of formulating and executing our response plan.
The goal here is to maintain oversight and accuracy over how we implement our response. For example, using project boards.
Most IT teams rely on templating to formulate responses to specific incidents. For example, we might have a pre-defined flow of tasks around identifying, categorizing, diagnosing, and righting incidents.
This also helps us to track the associated costs of restoring services when incidents occur, helping to create a business case for process changes in the aftermath.
Asset management tools
Lastly, asset management tools are helpful for predicting, preventing, identifying, and responding to IT incidents.
By creating a centralized overview of our IT hardware estate, asset management tools play a central role in understanding our vulnerabilities and formulating plans to mitigate the impact of incidents.
For example, identifying areas of redundancy or contingency planning, especially if we need to redirect assets from one area to another in order to restore services.
Asset management tools also help us to prevent incidents by keeping on top of the maintenance, repair, and retirement needs of individual assets, as well as facilitating tasks like patch management and regular servicing.
Budibase for ITSM teams
Budibase is the open-source, low-code platform that enables IT teams to turn data into action.
With extensive external data support, streamlined visual design tools, powerful automations, optional self-hosting, free SSO, and more, Budibase is the ideal platform for solutions architects, data professionals, systems engineers, and other IT pros that need to ship professional tools at pace.
Enterprises all over the world choose Budibase to build secure, performant internal tools on top of their existing data and deliver best-in-class services to colleagues.
Check out our features overview to learn more.